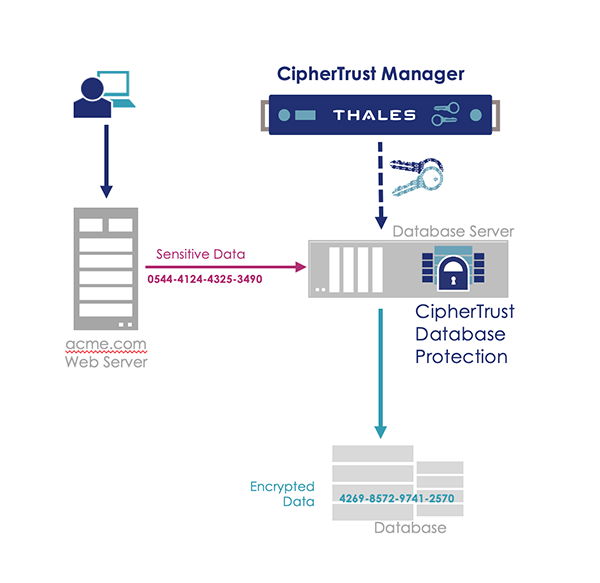
• Transparent Pprotection is delivered using native database triggers and views. The effect: no application changes are required for read or write activities.
• Granular access controls ensure only authorised users or applications can view protected data. Granularity can be assured with a specific key for each column, and CipherTrust Manager provides a range of powerful access controls for each key while simultaneously assuring separation of duties, a crucial aspect of data security. A downstream effect of these controls is prevention of database administrators gaining access to encrypted data.
• Built-in key rotation and data rekeying enables you to gain security with the possibility of actually reducing your workload for higher aggregate IT efficiency.
• Cloud-friendly software you can deploy on-premises and in private or public cloud environments and Chef recipes get the solution up and running fast.